Tinker, tailor, soldier, spy. And then there's Edward Snowden, who was a spy and then became something else. Nobody's neutral about him. The other day I heard a senior military officer describe him unambiguously as "a thief". In Washington he seems to be universally regarded as a traitor. Many people in Europe regard him as, at worst, a principled whistleblower and, at best, a hero in the Daniel Ellsberg mould.
Whatever you think about him, though, one thing is clear: Snowden is a pretty astute geek. The evidence for this is in the way he approached his whistleblowing task. Having concluded (as several other distinguished National Security Agency employees before him had) that the NSA had misinterpreted or overstepped its brief, he then identified prominent instances of agency overreach and for each category downloaded evidence that supported his conjecture.
We're now getting to the point where we can begin to assess the bigger picture. What do the Snowden revelations tell us about what's wrong with the NSA – and its leading overseas franchise, our own dear GCHQ?
The first, and most glaring, realisation is that the so-called democratic "oversight" of these intelligence agencies is so inadequate as to be effectively non-existent. And before Sir Malcolm Rifkind chokes on his muesli I should add that this is not because he and his kind – all those legislators and officials involved in this "oversight" – are lazy, corrupt or incompetent. The likelihood is that most of the stout parties involved in the oversight charade are conscientiously implementing the rules as they see them.
The problem is that the system of rules for ensuring that networked intelligence agencies stay on the right side of the line are ludicrously obsolete in relation to the technologies and the geeks that they are supposed to regulate. With computing power doubling every two years, bandwidth tripling and storage capacity quadrupling every year, any set of rules formulated in any given year is going to be looking out of date within three and laughable in five.
The second thing that emerges from the Snowden revelations is how catastrophic the concept of the "war on terror" has been. Normally, when a country declares war, a set of accepted legal conventions comes into force, and the populace simply has to put up with them. In 1939, for example, HMG became effectively omnipotent within the borders of the UK. The government could do whatever it deemed necessary, right down to requisitioning any piece or item of private property for a military purpose. Civil liberties were suspended. Censorship was comprehensive. It was, of course, draconian, but people knew where they stood. And they knew who the enemy was.
Bush's (and Blair's) "war" on terror was not a war in that sense. It was, and remains, a purely rhetorical device, and it has no constitutional standing compared with what happens in real wars. But it has provided the security services with a rationale for claiming warlike freedoms of action. We see that particularly in the NSA as unveiled by Snowden. As the security expert Bruce Schneier (who has seen many if not all of the Snowden documents) puts it, the agency has "commandeered the internet" in much the same way that wartime administrations commandeered cargo vessels, country estates and railway networks. In other words, it has treated the internet as though it owned it.
The starkest aspect of this is the way the NSA infiltrated (and therefore weakened) the encryption systems routinely employed to enable – and protect – online commerce and other legitimate online processes. Inserting back doors into these systems and undermining them in other ways are the kinds of actions that governments undertake in wartime, but which would be totally unacceptable otherwise. And of course in this case the actions have had the side effect of undermining trust in US companies, which dominate the internet. So the wartime mindset of the NSA may in the long run turn out to have been a colossal own goal.
As far as the NSA's geeks are concerned, some of the PowerPoint slides detailing what the agency and its UK franchise have been up to strike a chord. Anyone who works with programmers knows how they delight in pulling off clever stunts – showing how they have been able to do something difficult or exotic by writing ingenious code. In the business, such feats are known as "neat hacks", and they are widely esteemed by coders' peers.
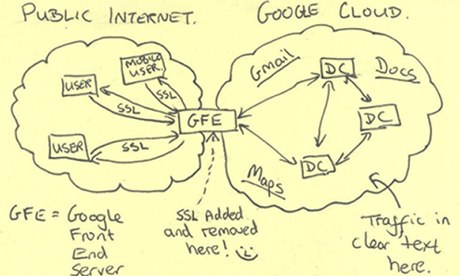
Recently, Ed Snowden published a slide from an NSA PowerPoint deck that detailed one such wheeze. It showed how the NSA had managed to tap into the (encrypted) data traffic flowing between Google's server farms. The slide shows – using a dotted line – the point at which the NSA has found a way of tapping into this supposedly protected traffic. "SSL added and removed here!" reads a scrawled note, followed by a smiley face, indicating that the authors saw it as a really neat hack. And these are the guys whom Rifkind and his American counterparts think they can control. Dream on.

